
👋 Hey there, I’m Dheeraj Choudhary an AI/ML educator, cloud enthusiast, and content creator on a mission to simplify tech for the world.
After years of building on YouTube and LinkedIn, I’ve finally launched TechInsight Neuron a no-fluff, insight-packed newsletter where I break down the latest in AI, Machine Learning, DevOps, and Cloud.
🎯 What to expect: actionable tutorials, tool breakdowns, industry trends, and career insights all crafted for engineers, builders, and the curious.
🧠 If you're someone who learns by doing and wants to stay ahead in the tech game you're in the right place.

Where Terraform Secrets Typically Leak
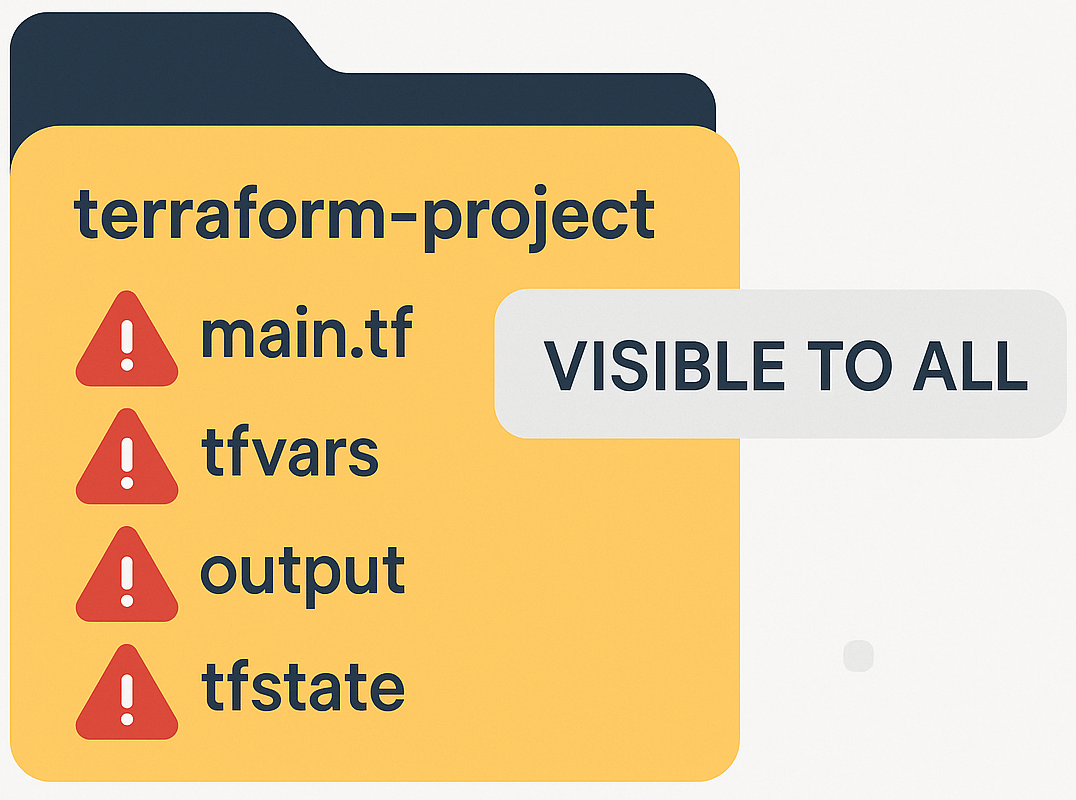
Before we fix the issue, let’s look at where secrets often get exposed:
Source | Example |
|---|---|
Hardcoded in |
|
Committed |
|
Output blocks |
|
State files | Stored plaintext in |
Console screenshots |
|
How to Pass Secrets Securely in Terraform

1. Environment Variables
Terraform supports passing values from shell env vars:
export TF_VAR_db_password="MySecretPwd"
In your code:
variable "db_password" {
sensitive = true
}✅ No secrets stored in files.
⚠️ But be careful not to echo or log them in terminal or scripts.
2. .tfvars Files (Untracked)
Create a secrets.tfvars:
db_password = "MySecretPwd"
Then exclude from version control:
# .gitignore
secrets.tfvarsRun with:
terraform apply -var-file="secrets.tfvars"✅ Structured and flexible
⚠️ Risky if .tfvars gets committed
3. Using sensitive = true in Variables and Outputs
variable "db_password" {
sensitive = true
}
output "show_me" {
value = var.db_password
sensitive = true
}✅ Prevents secret from being shown in CLI output
⚠️ Still exists in state file unless handled securely.
How to Avoid Secrets in Terraform State Files
The .tfstate file records everything Terraform creates — including sensitive data.
To avoid secrets ending up in state:
✅ Don’t output secrets
✅ Don’t pass plaintext secrets into resource attributes that aren’t marked sensitive
✅ Use cloud-native secret managers when possible
✅ Use Terraform providers that integrate with Vault or AWS Secrets Manager
Example (Bad):
resource "aws_db_instance" "prod" {
username = "admin"
password = var.db_password # gets stored in state
}Workaround Options
Use
vaultprovider to fetch secrets on runtimeBootstrap secrets externally and reference IDs instead of values
Encrypt backend state (e.g., S3 + SSE, Terraform Cloud)
Using Vault with Terraform
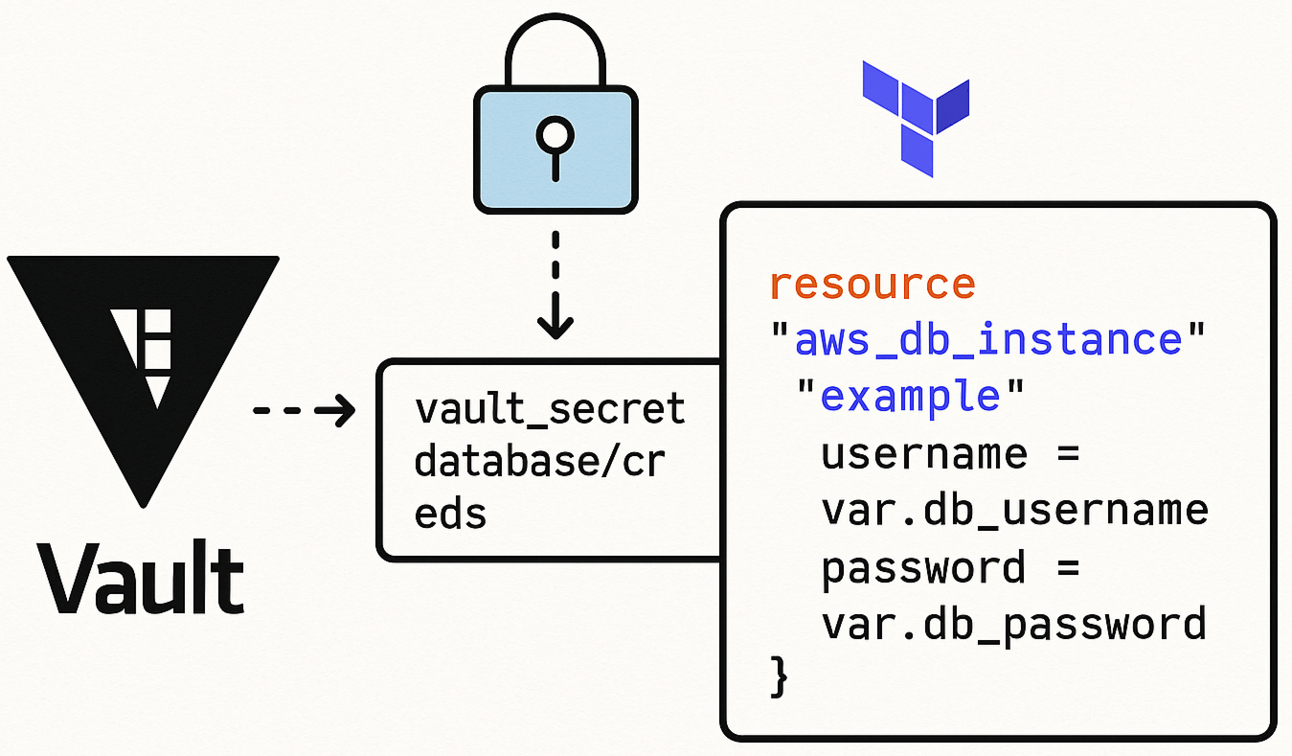
HashiCorp Vault can be used to dynamically fetch secrets.
provider "vault" {}
data "vault_generic_secret" "db_creds" {
path = "secret/data/db"
}Access it like:
resource "aws_db_instance" "db" {
username = data.vault_generic_secret.db_creds.data["username"]
password = data.vault_generic_secret.db_creds.data["password"]
}Encrypting State Files in the Backend
If secrets must live in state, encrypt the backend:
AWS S3:
encrypt = true
kms_key_id = "alias/my-key"Terraform Cloud:
State is encrypted by default
Uses workspace-based isolation
Secrets can be managed securely via the UI
Best Practices for Secret Management
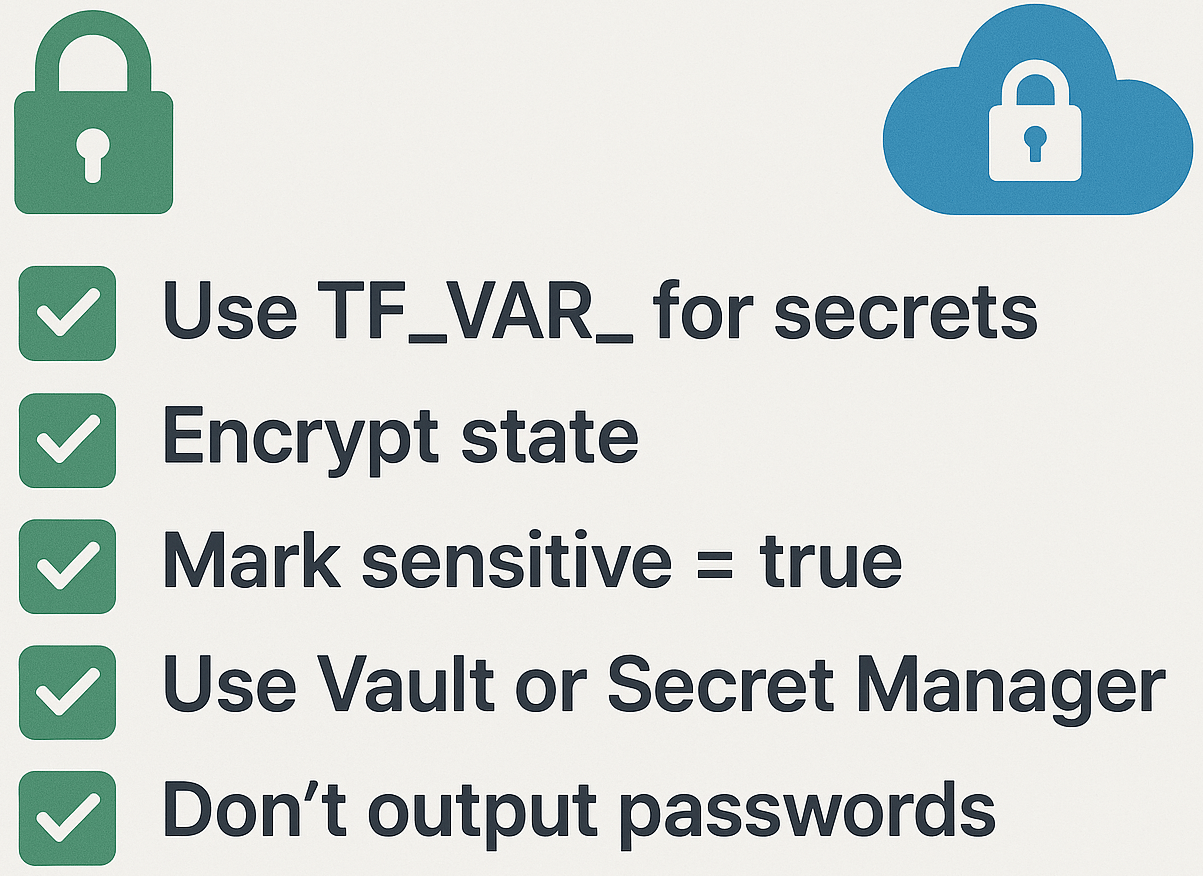
✅ Always set sensitive = true on secrets
✅ Avoid outputting secrets unless absolutely required
✅ Use environment variables or secret managers — not raw .tf
✅ Encrypt your backend state
✅ Audit your .tfstate for leaks before sharing
✅ Use separate service accounts/keys per environment
💡 Tip of the Day:
If you wouldn't post your Terraform config on Twitter your secrets don't belong in it. Use environment variables, encrypt state, and let secret managers do their job.
📚 Resources & References
1️⃣ Managing Sensitive Data in Terraform
🔗 Docs
Use of sensitive = true and input handling.
2️⃣ HashiCorp Vault Provider Docs
🔗 Vault Provider
How to fetch secrets dynamically.
3️⃣ Terraform and AWS Secrets Manager
🔗 Example
Using cloud-native secret stores.
4️⃣ Terraform CLI Sensitive Output Handling
🔗 CLI Docs
How sensitive outputs are hidden.
🔗Let’s Stay Connected
📱 Join Our WhatsApp Community
Get early access to AI/ML, Cloud & Devops resources, behind-the-scenes updates, and connect with like-minded learners.
➡️ Join the WhatsApp Group
✅ Follow Me for Daily Tech Insights
➡️ LinkedIN
➡️ YouTube
➡️ X (Twitter)
➡️ Website
Conclusion
Terraform gives you immense power but with power comes the responsibility of protecting your credentials, tokens, and keys.
Whether you’re using environment variables, .tfvars, or pulling secrets from Vault, the key is to never expose sensitive data by default. The risks are real: a leaked API key can bring down your infra, cost you thousands, or even get your account banned.
With best practices like marking variables sensitive, encrypting backends, and using proper secret sources, you’ll turn your Terraform project from risky to resilient.
Infrastructure as code doesn’t stop at automation it extends to security. And secrets are where that principle matters most.

