
👋 Hey there, I’m Dheeraj Choudhary an AI/ML educator, cloud enthusiast, and content creator on a mission to simplify tech for the world.
After years of building on YouTube and LinkedIn, I’ve finally launched TechInsight Neuron a no-fluff, insight-packed newsletter where I break down the latest in AI, Machine Learning, DevOps, and Cloud.
🎯 What to expect: actionable tutorials, tool breakdowns, industry trends, and career insights all crafted for engineers, builders, and the curious.
🧠 If you're someone who learns by doing and wants to stay ahead in the tech game you're in the right place.
What Is the lifecycle Block in Terraform?
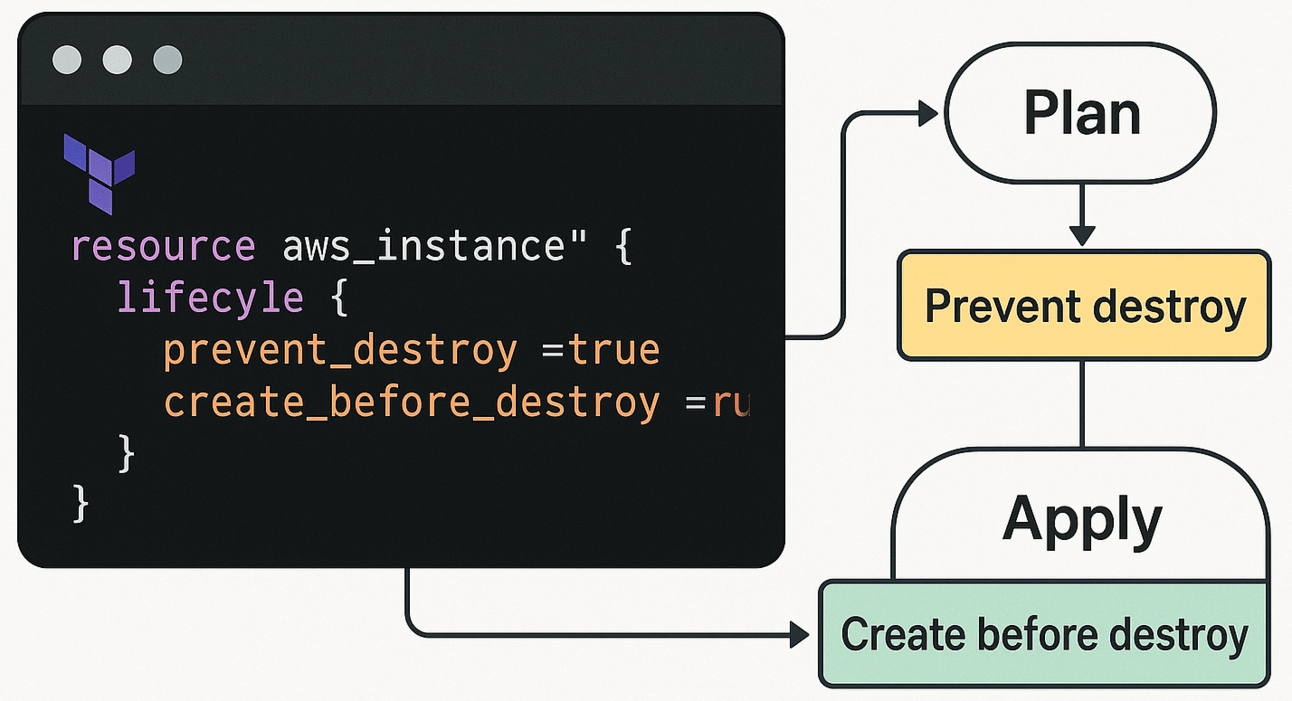
The lifecycle block is a meta-argument you can attach to any resource to tell Terraform how to behave during updates or destruction.
It lives inside the resource like this:
resource "aws_instance" "web" {
ami = "ami-0c55b159cbfafe1f0"
instance_type = "t3.micro"
lifecycle {
prevent_destroy = true
}
} It doesn't define what is created — it controls how Terraform handles that resource’s lifecycle.
1. prevent_destroy: Safety Net for Critical Resources
The most straightforward — and the most valuable.
lifecycle {
prevent_destroy = true
} This ensures the resource cannot be destroyed unless you explicitly override it.
🔧 Use cases:
Protecting production databases
Preventing deletion of VPCs, IAM users, or secrets
Making sure mistakes don’t wipe critical infra
⚠️ If you try to destroy it:
Error: Resource marked for prevent_destroyTo override, you must manually remove the flag and re-apply.
2. create_before_destroy: Zero-Downtime Deployments
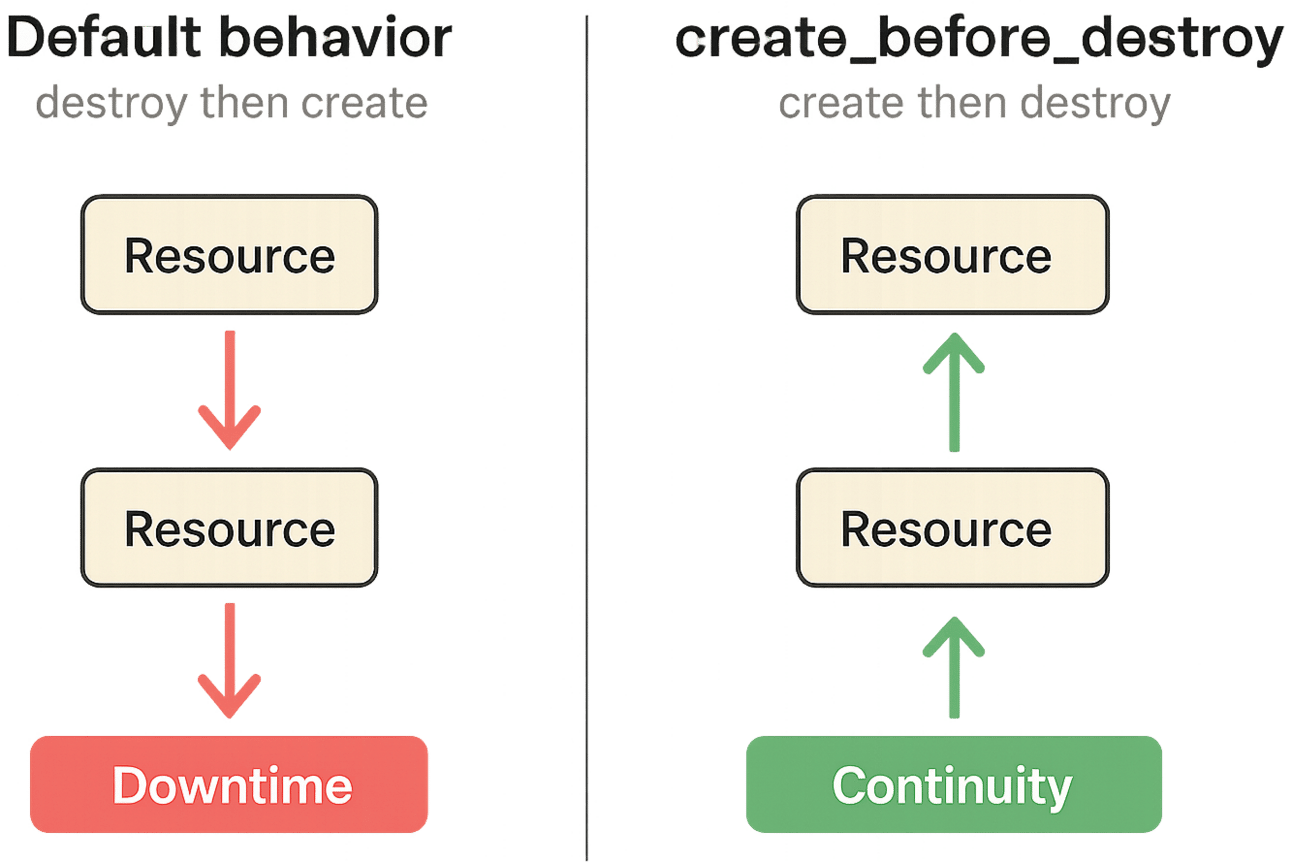
Sometimes Terraform needs to replace a resource — but the default behavior is to destroy first, then recreate.
This can cause downtime.
Instead, you can tell Terraform:
lifecycle {
create_before_destroy = true
}🔧 Use cases:
Load balancers or instances behind auto-scaling
EBS volumes or network interfaces that must remain available
Cloud services with immutable IDs or dependencies
⚠️ Be careful: this can result in resource duplication if not handled properly.
3. ignore_changes: Avoid Unwanted Diffs
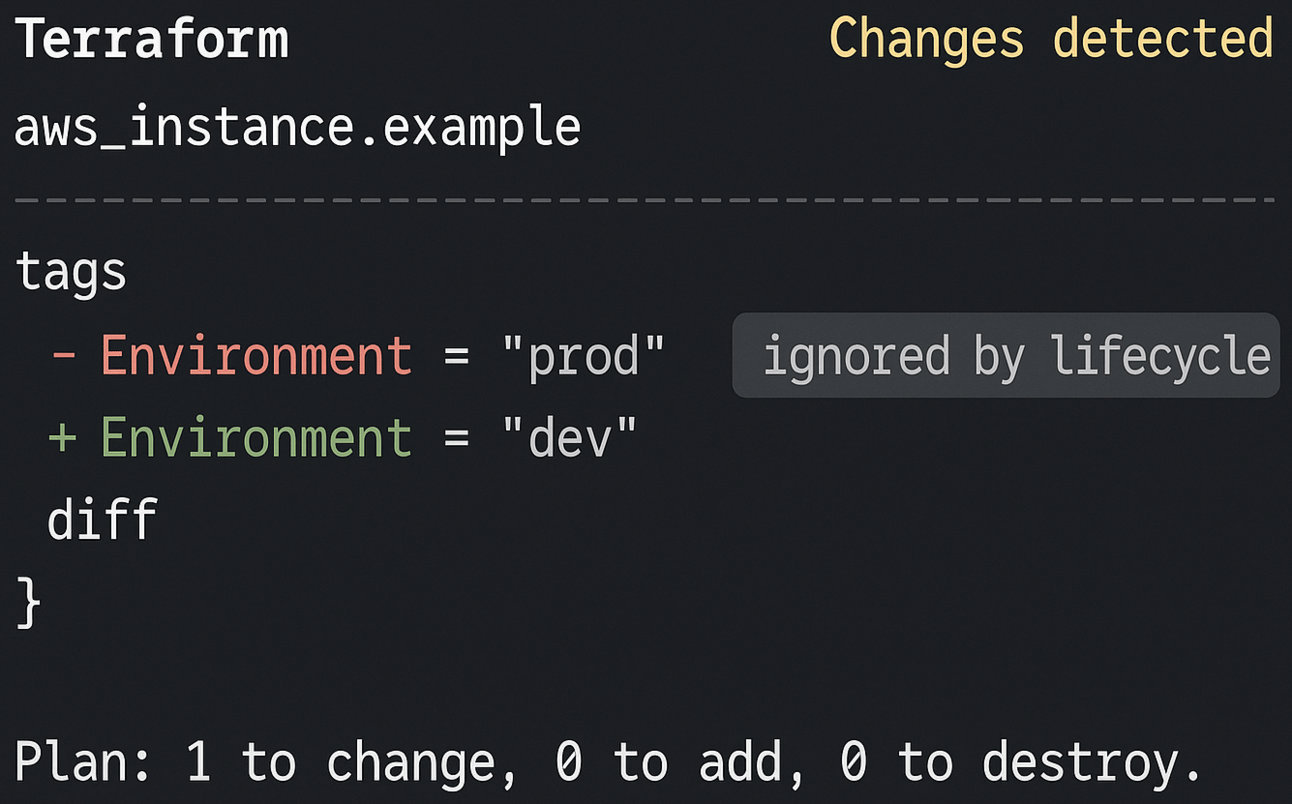
This flag tells Terraform to ignore changes to specific attributes — even if they differ from your config.
lifecycle {
ignore_changes = [ tags, user_data ]
}🔧 Use cases:
Resources with external systems modifying tags
CI/CD pipelines injecting dynamic environment variables
Preventing drift noise on non-critical attributes
⚠️ Don’t overuse it — this can hide real drift if abused.
How Lifecycle Flags Work Together
Yes you can combine them:
lifecycle {
prevent_destroy = true
create_before_destroy = true
ignore_changes = [ metadata ]
}Terraform will:
Refuse to destroy it
Create a replacement first (if needed)
Ignore certain fields during plan
But remember: more control = more responsibility. Always document why you’re using lifecycle rules.
Common Pitfalls
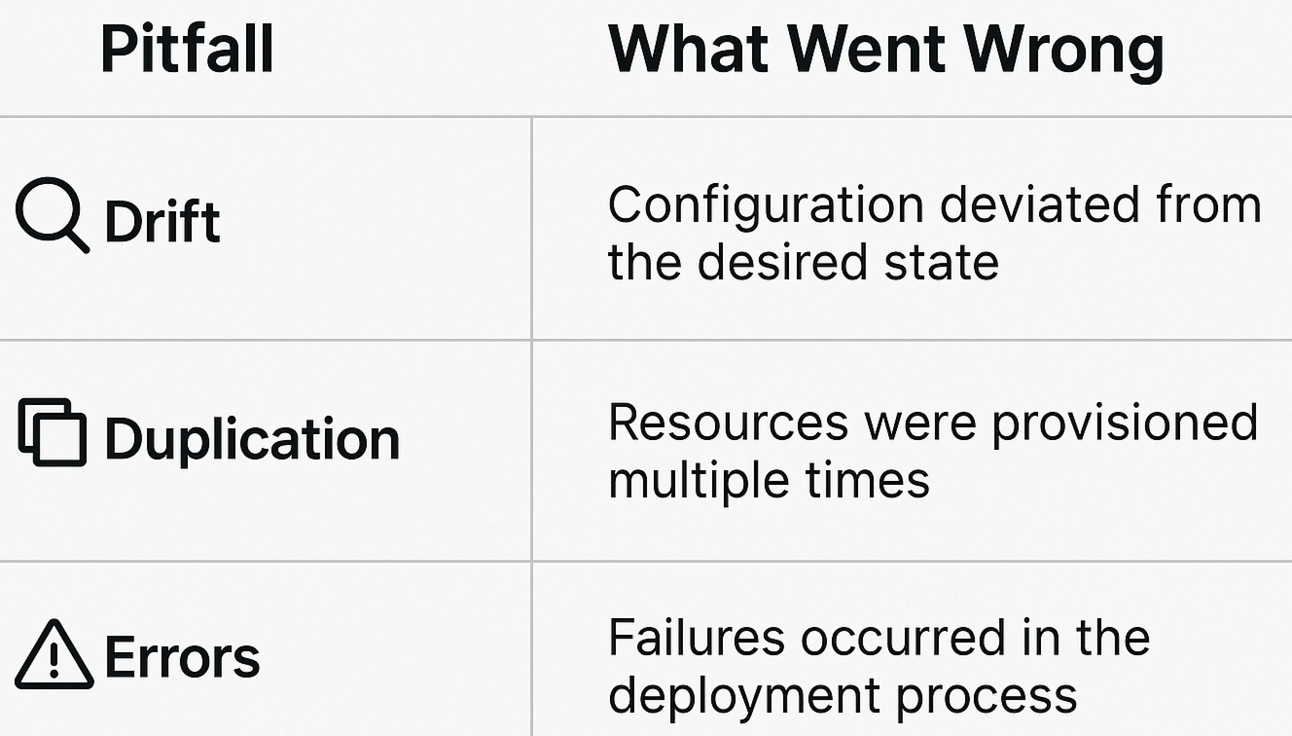
Pitfall | Why it happens | Fix |
|---|---|---|
Silent drift with | External system changes critical field | Review diffs regularly and audit outputs |
Blocked apply with | Accidentally removing resource | Manually remove flag with explanation |
Duplicate resources with | Dependencies not updated in time | Use explicit |
💡 Tip of the Day:
Use lifecycle rules to guide Terraform — not to micromanage it. Terraform’s strength is its declarative design. Lifecycle flags are the exception — use them when clarity or stability demands it, but always with caution.
📚 Resources & References
1️⃣ Terraform Lifecycle Meta-Arguments
🔗 Docs
Official reference for lifecycle behavior and syntax.
2️⃣ Understanding create_before_destroy
🔗 Best Practice
Avoiding downtime when replacing resources.
3️⃣ Dealing with prevent_destroy Failures
🔗 Community Guide
Tips for manually recovering when flagged.
4️⃣ Terraform Plan Visualization Tools
🔗 Tools
Render diffs and lifecycle effects visually in CI pipelines.
🔗Let’s Stay Connected
📱 Join Our WhatsApp Community
Get early access to AI/ML, Cloud & Devops resources, behind-the-scenes updates, and connect with like-minded learners.
➡️ Join the WhatsApp Group
✅ Follow Me for Daily Tech Insights
➡️ LinkedIN
➡️ YouTube
➡️ X (Twitter)
➡️ Website
Conclusion
Terraform’s lifecycle meta-arguments give you precise control over how and when resources change without breaking Terraform’s declarative model.
Used wisely, they:
Prevent accidental destruction of critical resources
Eliminate downtime in replacements
Mute false-positive diffs from dynamic systems
But they can also hide drift, block changes, or create infrastructure clutter if overused.
The best Terraform engineers treat lifecycle like a safety override, not a default pattern. It’s there to protect, not to control.
As you scale Terraform usage across teams and stacks, mastering lifecycle behavior is what separates script writers from infrastructure engineers.

