
👋 Hey there, I’m Dheeraj Choudhary an AI/ML educator, cloud enthusiast, and content creator on a mission to simplify tech for the world.
After years of building on YouTube and LinkedIn, I’ve finally launched TechInsight Neuron a no-fluff, insight-packed newsletter where I break down the latest in AI, Machine Learning, DevOps, and Cloud.
🎯 What to expect: actionable tutorials, tool breakdowns, industry trends, and career insights all crafted for engineers, builders, and the curious.
🧠 If you're someone who learns by doing and wants to stay ahead in the tech game you're in the right place.
What Is a Terraform Backend?
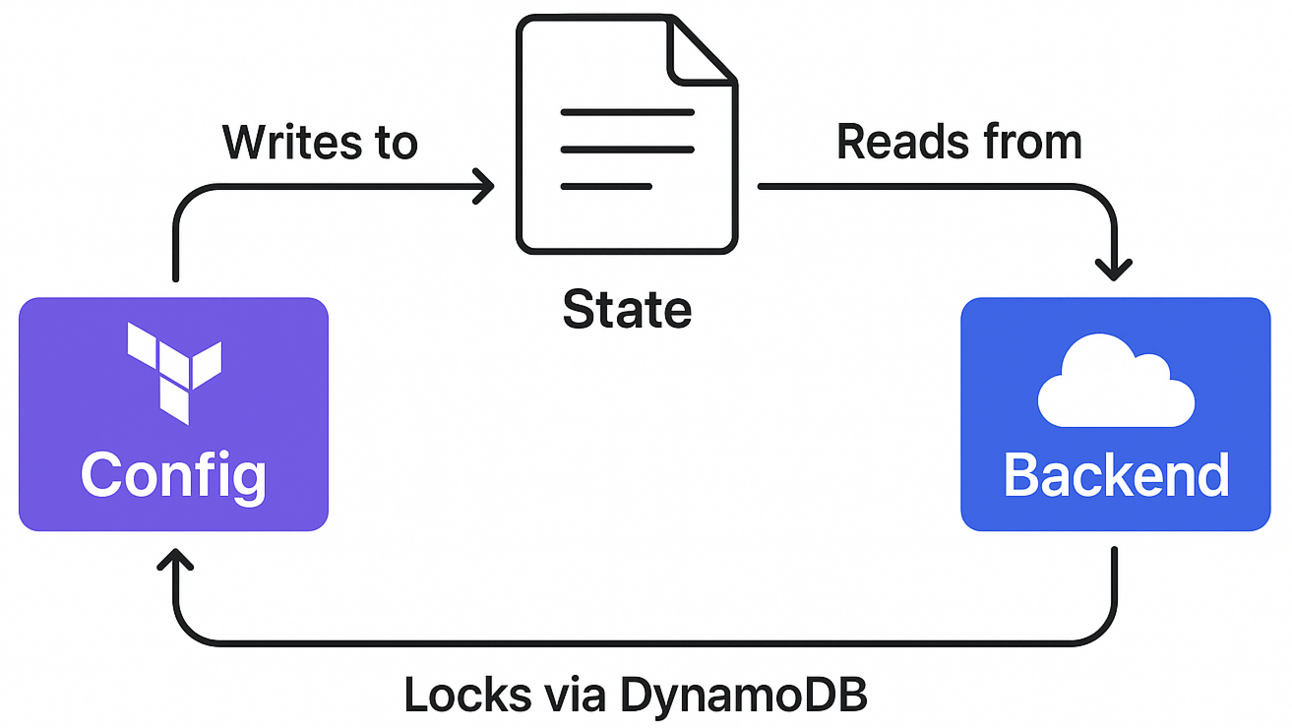
A backend in Terraform is where Terraform stores, reads, and writes state.
By default, Terraform uses the local backend, which stores state on your local machine:
./terraform.tfstate This works fine for personal projects, but becomes dangerous in production because:
There’s no collaboration
No state locking
No versioning
No remote backup
Instead, you should configure a remote backend.
Supported Terraform Backend Types
Here are some of the most common backends you can use:
Backend Type | Description |
|---|---|
| Default file on disk |
| AWS S3 bucket with optional DynamoDB locking |
| Google Cloud Storage |
| Azure Blob Storage |
| Generic HTTP endpoint |
| Uses Consul key/value store |
| HashiCorp Terraform Cloud or Enterprise backend |
Each has its own setup, permissions, and trade-offs.
Example: S3 + DynamoDB Backend Configuration
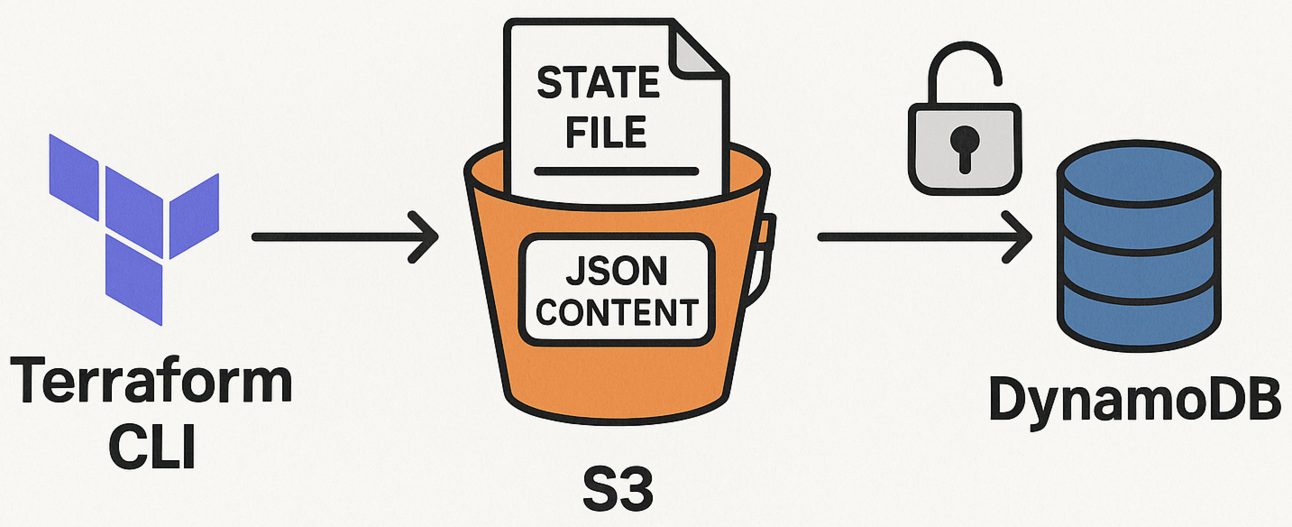
Let’s look at one of the most popular setups: AWS S3 with DynamoDB for state locking.
Step 1: Create S3 Bucket + DynamoDB Table
aws s3api create-bucket --bucket tf-backend-demo --region us-east-1
aws dynamodb create-table \
--table-name tf-state-locks \
--attribute-definitions AttributeName=LockID,AttributeType=S \
--key-schema AttributeName=LockID,KeyType=HASH \
--billing-mode PAY_PER_REQUESTStep 2: Add to main.tf
terraform {
backend "s3" {
bucket = "tf-backend-demo"
key = "global/s3/terraform.tfstate"
region = "us-east-1"
dynamodb_table = "tf-state-locks"
encrypt = true
}
}💡 This block must not contain interpolations or variables.
Step 3: Initialize the Backend
terraform init Terraform will prompt to migrate existing state. Confirm with yes.
Common Backend Misconfigurations
Issue | Cause | Solution |
|---|---|---|
Interpolation in backend block | Variables used in backend config | Use hardcoded values only |
Permission denied | IAM policy missing for S3/DynamoDB | Add |
Backend mismatch | Two projects using different backends | Align or manually migrate state |
Locked state file | Another session holds the lock | Wait or manually unlock (use cautiously) |
Best Practices for Backend Management
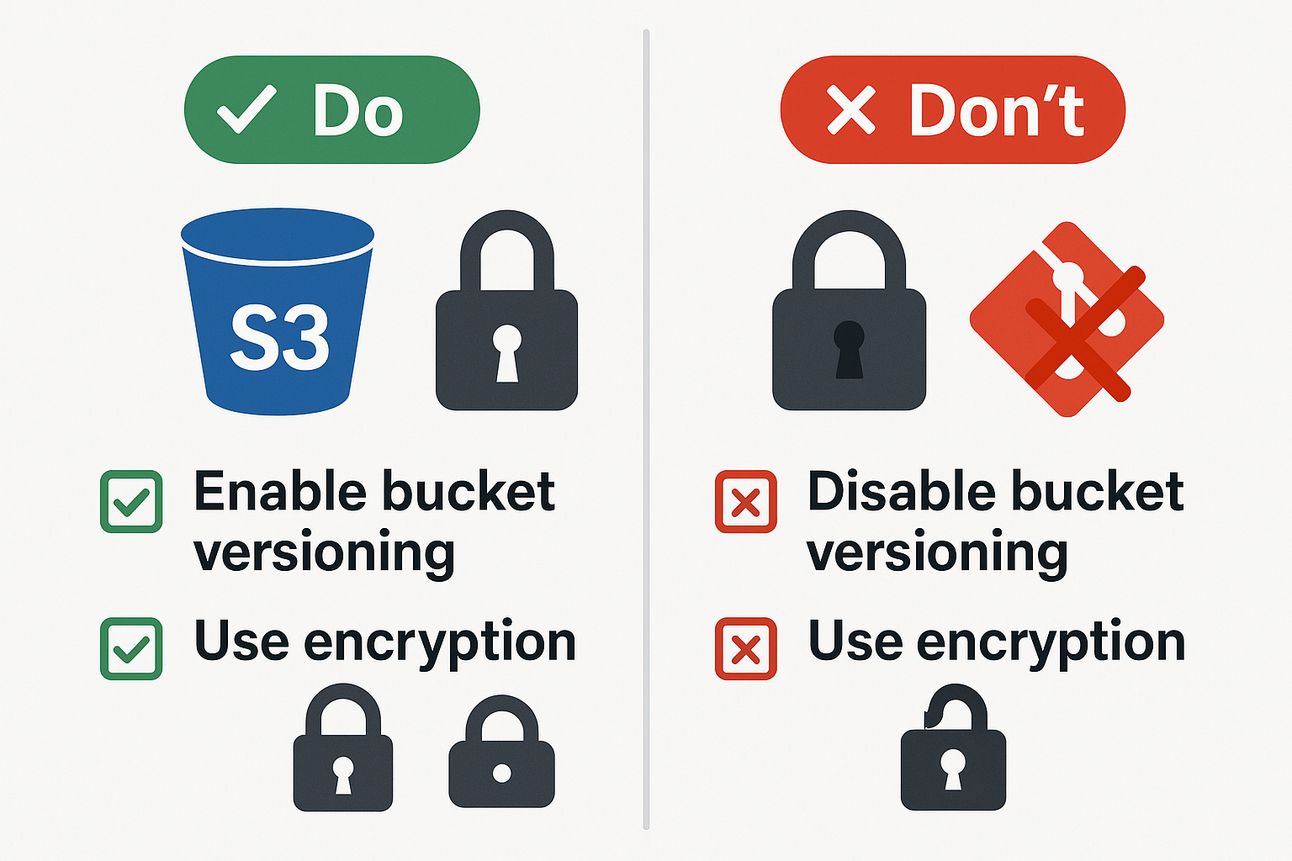
✅ Always use remote state in team projects
✅ Enable locking (e.g., with DynamoDB or built-in Terraform Cloud)
✅ Set versioning on your backend bucket
✅ Use separate folders/keys per environment
✅ Keep sensitive outputs encrypted and secure
❌ Never share or commit .tfstate files
❌ Never modify the state file manually
Migrating from Local to Remote Backend
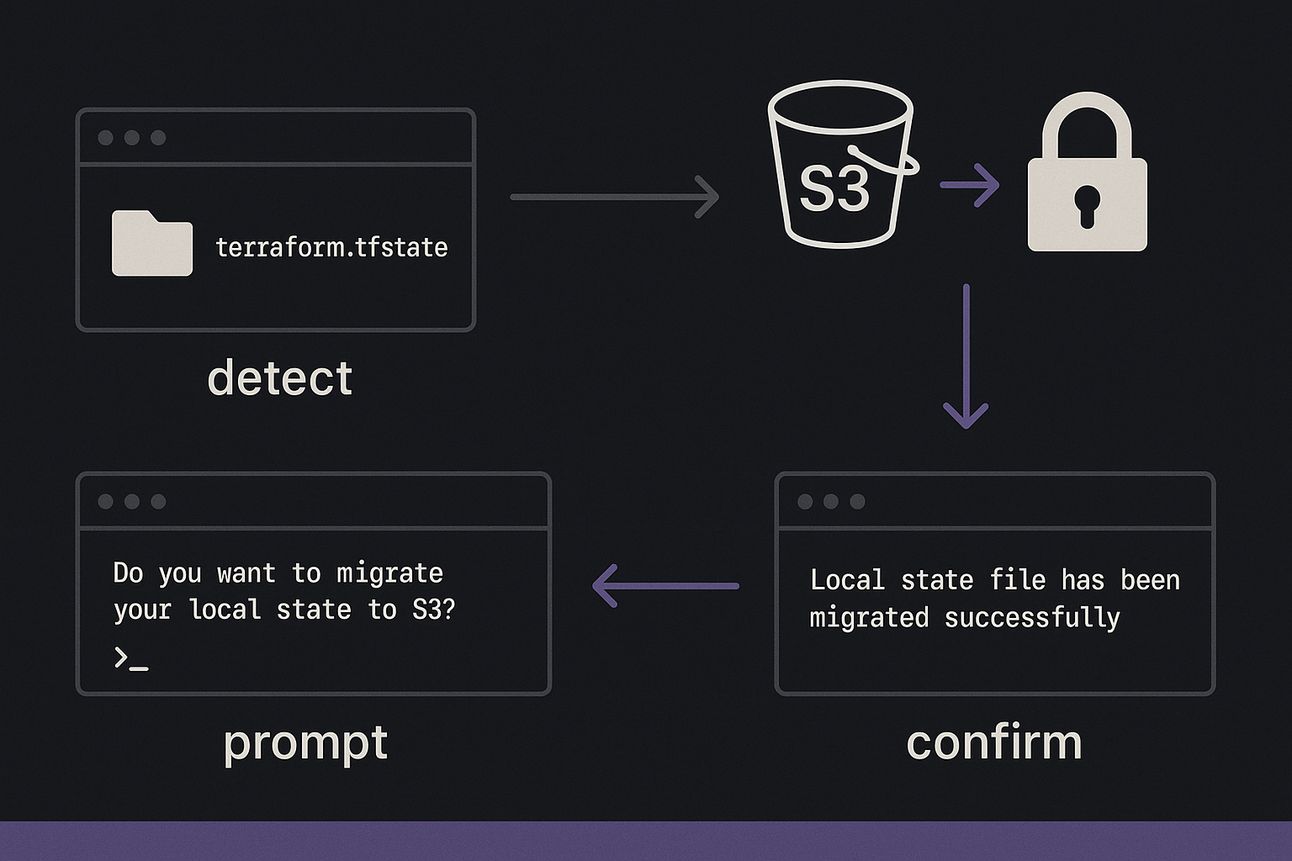
Already started with local? Here's how to migrate safely:
Define the
backendblock in your configRun:
terraform init Terraform will detect existing local state and offer to migrate
Say
yesto move it to your remote backendBackup your old
terraform.tfstatejust in case
✅ Done. You’re now remote-first.
💡 Tip of the Day:
Your backend defines how your Terraform project scales. A local .tfstate works until it doesn't. Migrate early, lock it down, and treat it like infrastructure's brain because that’s exactly what it is.
📚 Resources & References
1️⃣ Terraform Backend Configuration Docs
🔗 Docs
In-depth guide to backend types, syntax, and behavior.
2️⃣ Using S3 + DynamoDB as Backend
🔗 Doc
Secure remote backend with locking, versioning, encryption.
3️⃣ Terraform Init Command
🔗 CLI Docs
What happens when you initialize backends.
4️⃣ Terraform Cloud Remote Backend
🔗 Doc
Backend managed by HashiCorp with UI and versioning.
🔗Let’s Stay Connected
📱 Join Our WhatsApp Community
Get early access to AI/ML, Cloud & Devops resources, behind-the-scenes updates, and connect with like-minded learners.
➡️ Join the WhatsApp Group
✅ Follow Me for Daily Tech Insights
➡️ LinkedIN
➡️ YouTube
➡️ X (Twitter)
➡️ Website
Conclusion
The backend is one of the least visible, but most critical parts of a Terraform setup.
It defines how Terraform stores, accesses, and protects your infrastructure state. Whether you're working solo or with a team, choosing and configuring the right backend is essential for maintaining integrity, security, and collaboration.
Don't treat backend configuration as optional boilerplate treat it as infrastructure for your infrastructure. Because when your state is mismanaged, everything built on top of it becomes unstable.
With the right backend setup — remote, versioned, encrypted, and locked Terraform becomes the reliable, scalable tool it was designed to be.

